Introduction: The Challenge of Securing a Massive Kafka Deployment
Uber operates one of the largest Kafka deployments in the world, handling an astonishing 138 million messages per second across 38 clusters. Given the scale and criticality of these systems, ensuring their security is paramount. To address this challenge, Uber implements a robust security strategy centered around mTLS (mutual TLS) and strong authorization rules.
In this guide, we’ll explore how Uber secures its Kafka deployment using mTLS, Spire for identity management, and Charter for authorization. We’ll dive into the architecture, key components, and best practices that enable Uber to maintain a secure and scalable Kafka environment.
Kafka and the Need for Security
Kafka is a distributed event streaming platform that powers a wide range of real-time data pipelines and streaming applications. At Uber’s scale, securing Kafka is not just about protecting data; it’s about ensuring that only authorized services can communicate, and that even if a service is compromised, the potential damage is minimized.
Uber’s approach to security involves treating its production environment as a zero-trust network, where no entity is implicitly trusted, and every interaction must be authenticated and authorized.
mTLS: Establishing Strong Authentication and Confidentiality
mTLS (mutual TLS) is a critical component of Uber’s security architecture. It ensures that both the client and server authenticate each other before any data is exchanged, providing authentication, confidentiality, and data integrity.
How mTLS Works in Uber’s Kafka Deployment
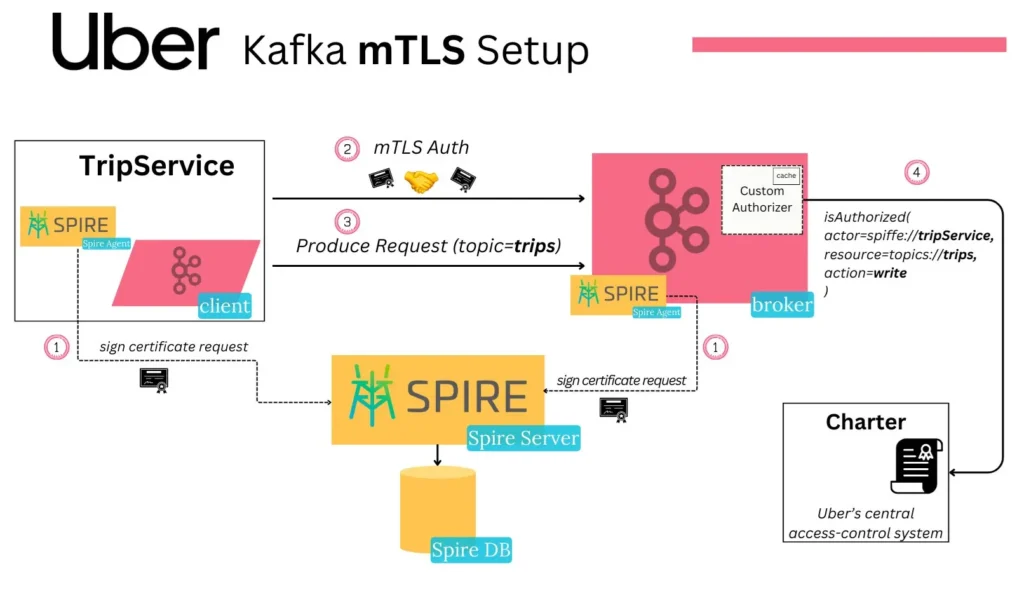
1. Certificate Request Signing:
The process begins with the Spire Agent in the TripService (client) and the Kafka broker. The agent requests a certificate from the Spire Server, which is responsible for issuing and managing short-lived, auto-rotated cryptographic key pairs.
Key Components:
X.509-SVID: A cryptographic identity issued by the Spire Server.
Private Key: A secure key held by the client or broker.
Trust Bundle: A collection of trusted certificates.
Code Example:
bash
spire-agent api fetch x509 --write ./path-to-cert
2. mTLS Authentication:
Once certificates are issued, mTLS authentication is performed when the client (TripService) initiates a connection to the Kafka broker. Both the client and broker verify each other’s identities using the certificates, establishing a secure channel.
Key Benefits:
Authentication: Ensures that the client and broker are who they claim to be.
Confidentiality: Encrypts the communication channel, protecting data in transit.
Integrity: Ensures that data has not been tampered with during transmission.
3. Produce Request:
After successful authentication, the TripService sends a produce request to the Kafka broker to write data to the trips topic.
Code Example:
javascript
const kafka = new Kafka({
clientId: 'tripService',
brokers: ['broker:9092'],
ssl: true,
sasl: {
mechanism: 'scram-sha-256',
username: 'user',
password: 'pass'
}
});
const producer = kafka.producer();
await producer.connect();
await producer.send({
topic: 'trips',
messages: [
{ key: 'tripKey', value: 'tripData' }
]
});
Spire: Managing Identity and Certificates
At the heart of Uber’s security setup is Spire, a platform based on the SPIFFE (Secure Production Identity Framework for Everyone) specification. Spire is responsible for managing identities and issuing certificates that are integral to the mTLS process.
Key Features of Spire:
Short-lived Certificates:
Spire issues short-lived certificates that are automatically rotated before expiry. This minimizes the risk if a certificate is compromised, as the time window for misuse is limited.Proactive Certificate Renewal:
The Spire agent maintains a long-lived connection with the Spire server, allowing it to proactively renew certificates as needed.Trust Management:
Spire manages a trust bundle that ensures all parties in the communication chain trust each other’s certificates.
Charter: Authorization with Fine-Grained Control
While mTLS provides strong authentication, it doesn’t address authorization—ensuring that a service is permitted to perform specific actions on a resource. This is where Charter, Uber’s central access-control system, comes into play.
How Charter Works:
- Authorization Request:
When the Kafka broker receives a produce request, it triggers the Custom Authorizer. This authorizer, integrated into Kafka’s pluggable authorization framework, makes an authorization decision based on the actor, resource, and operation.
Example:
json
{
"isAuthorized": {
"actor": "spiffe://tripService",
"resource": "topics://trips",
"action": "write"
}
}
Charter Integration:
The Custom Authorizer sends a remote RPC call to Charter to determine if the action is permitted. Charter evaluates the request based on predefined policies and returns an authorization decision.
- Caching:
To improve performance, the authorization results are cached, reducing the need for repeated calls to Charter for the same authorization checks.
Key Benefits of Uber’s Kafka Security Model
Zero-Trust Network:
By treating every entity as potentially untrustworthy, Uber ensures that only authenticated and authorized services can interact, significantly reducing the risk of unauthorized access.Strong Cryptographic Security:
The use of mTLS and short-lived certificates issued by Spire provides strong authentication, encryption, and data integrity, safeguarding sensitive information as it flows through Kafka.Fine-Grained Authorization:
Charter provides a flexible and powerful framework for managing who can access what, ensuring that only authorized actions are performed on Kafka resources.
Conclusion: Securing Kafka at Scale
Uber’s approach to securing its Kafka deployment is a textbook example of how to build a secure and resilient data streaming platform at scale. By combining mTLS, Spire, and Charter, Uber creates a robust security model that not only authenticates and encrypts communications but also enforces strict authorization rules.
For organizations looking to secure their Kafka deployment, adopting a similar approach with strong authentication, encryption, and fine-grained authorization is crucial. This not only protects sensitive data but also ensures that only authorized services can interact, reducing the attack surface and enhancing overall security.