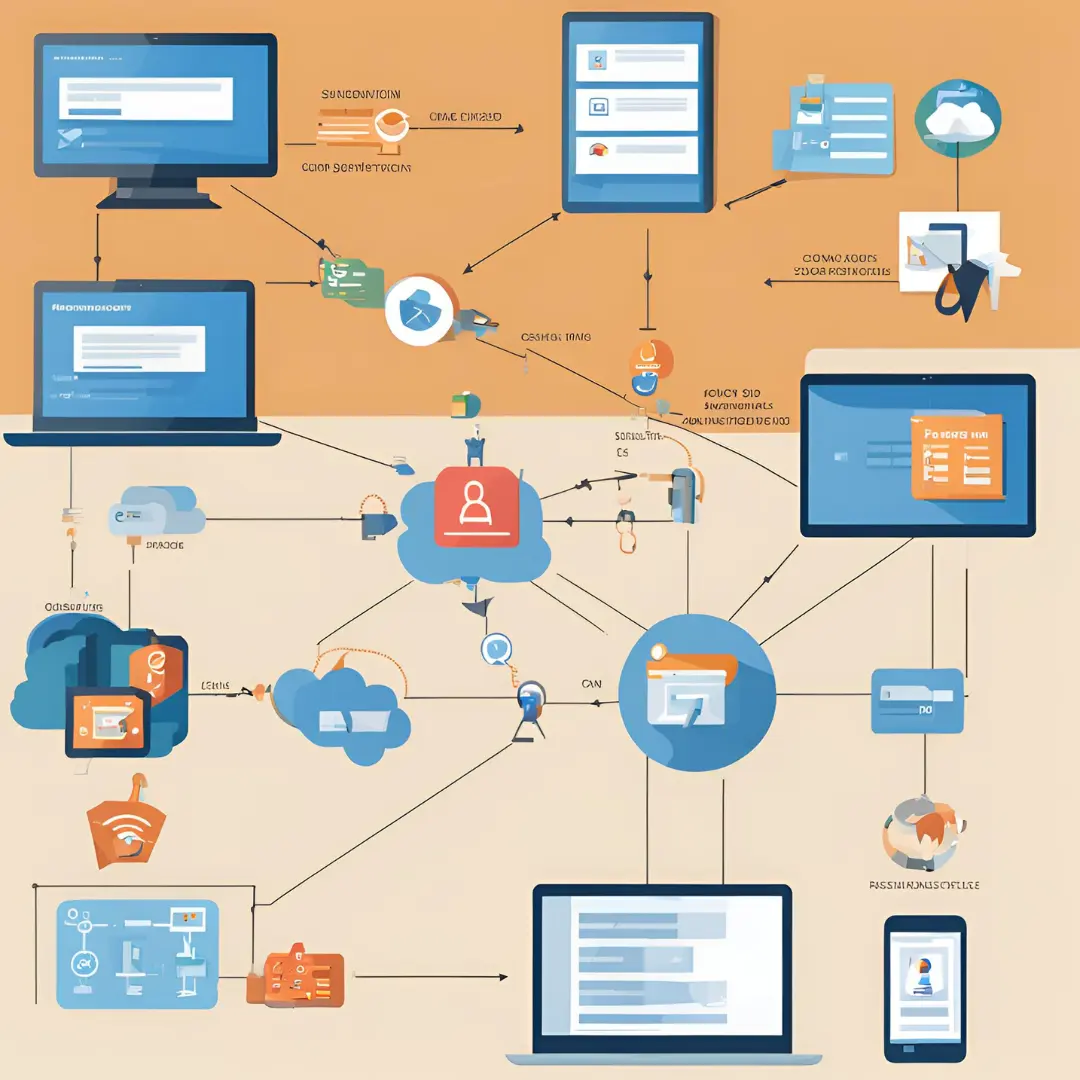
Single Sign-On (SSO) is an authentication process that allows a user to access multiple applications with one set of login credentials. This mechanism improves the user experience by reducing the need to log in multiple times for different services, enhancing security by centralizing authentication processes, and simplifying management for administrators.
How SSO Works
SSO operates by establishing a centralized authentication server that manages user credentials and sessions. When a user attempts to access an application, the application delegates the authentication process to the SSO server. If the user is already authenticated, the SSO server grants access without requiring a new login. If not, the user is prompted to authenticate.
Key Components
SSO Login Page: The centralized interface where users enter their login credentials.
SSO Authentication Server: The server responsible for verifying user credentials and maintaining authentication tokens.
Applications (e.g., Gmail, YouTube): The services that users access using SSO.
Benefits of SSO
Enhanced User Experience: Users log in once and gain access to multiple services.
Improved Security: Centralized authentication reduces the risk of weak passwords and phishing.
Simplified Management: Administrators manage a single set of credentials for multiple applications.
Detailed Explanation of the SSO Process
Let’s break down the SSO process using an example involving two applications, Gmail and YouTube, with Gmail being in Domain 1 and YouTube in Domain 2. Here’s how the SSO process works:
Step-by-Step Process
- User Enters Login Credentials:
- The user navigates to Gmail (Domain 1) and enters their login credentials on the SSO Login Page.
- Request Authentication:
- Gmail sends an authentication request to the SSO Authentication Server.
- Create Token and Global Session:
- The SSO Authentication Server verifies the credentials. If valid, it creates an authentication token and establishes a global session for the user.
- Authenticate with Token:
- The SSO Authentication Server sends the token back to Gmail.
- Register System (Gmail):
- Gmail registers the user session with the received token.
- Token Validated:
- The token is validated by Gmail, allowing the user to access protected resources within Gmail.
- Return Protected Resources:
- Gmail returns the protected resources, granting the user access to their Gmail account.
- Navigate from Gmail to YouTube:
- The user decides to switch to YouTube (Domain 2).
- Request Authentication:
- YouTube sends an authentication request to the SSO Authentication Server, similar to the initial Gmail request.
- Already Logged In:
- The SSO Authentication Server recognizes that the user is already logged in due to the existing global session.
- Authenticate with Token:
- The SSO Authentication Server sends the existing token to YouTube.
- Register System (YouTube):
- YouTube registers the user session with the received token.
- Token Validated:
- The token is validated by YouTube, granting access to the user.
- Return Protected Resources:
- YouTube returns the protected resources, allowing the user to access their YouTube account without needing to re-enter login credentials.
Key Points to Note
Single Authentication Point: Users only need to authenticate once with the SSO Authentication Server to gain access to multiple applications.
Token-Based Authentication: The SSO server issues a token upon successful authentication, which is used by applications to validate the user.
Session Management: The SSO server maintains a global session, enabling seamless access to various services without repeated logins.
Security Considerations
Centralized Authentication: While SSO simplifies access, it also means that a breach in the SSO system could compromise multiple services.
Token Security: Ensuring tokens are securely transmitted and stored is critical to prevent unauthorized access.
Real-World Examples
Google Services: Accessing Gmail, Google Drive, and YouTube with a single Google account.
Microsoft Services: Using one Microsoft account for Outlook, OneDrive, and other Microsoft applications.
Conclusion: Understanding Single Sign-On (SSO)
Single Sign-On (SSO) is a powerful authentication mechanism that enhances user experience by allowing access to multiple services with a single set of credentials. By centralizing the authentication process, SSO improves security and simplifies credential management. Understanding the SSO workflow, from login to resource access, highlights the efficiency and convenience it brings to modern web applications.