As the software development landscape continues to evolve, so too must the practices that ensure the security and integrity of the software being developed. DevSecOps has emerged as a natural progression of DevOps, integrating security at every stage of the software development lifecycle. But what is DevSecOps, and why is it crucial for modern software development?
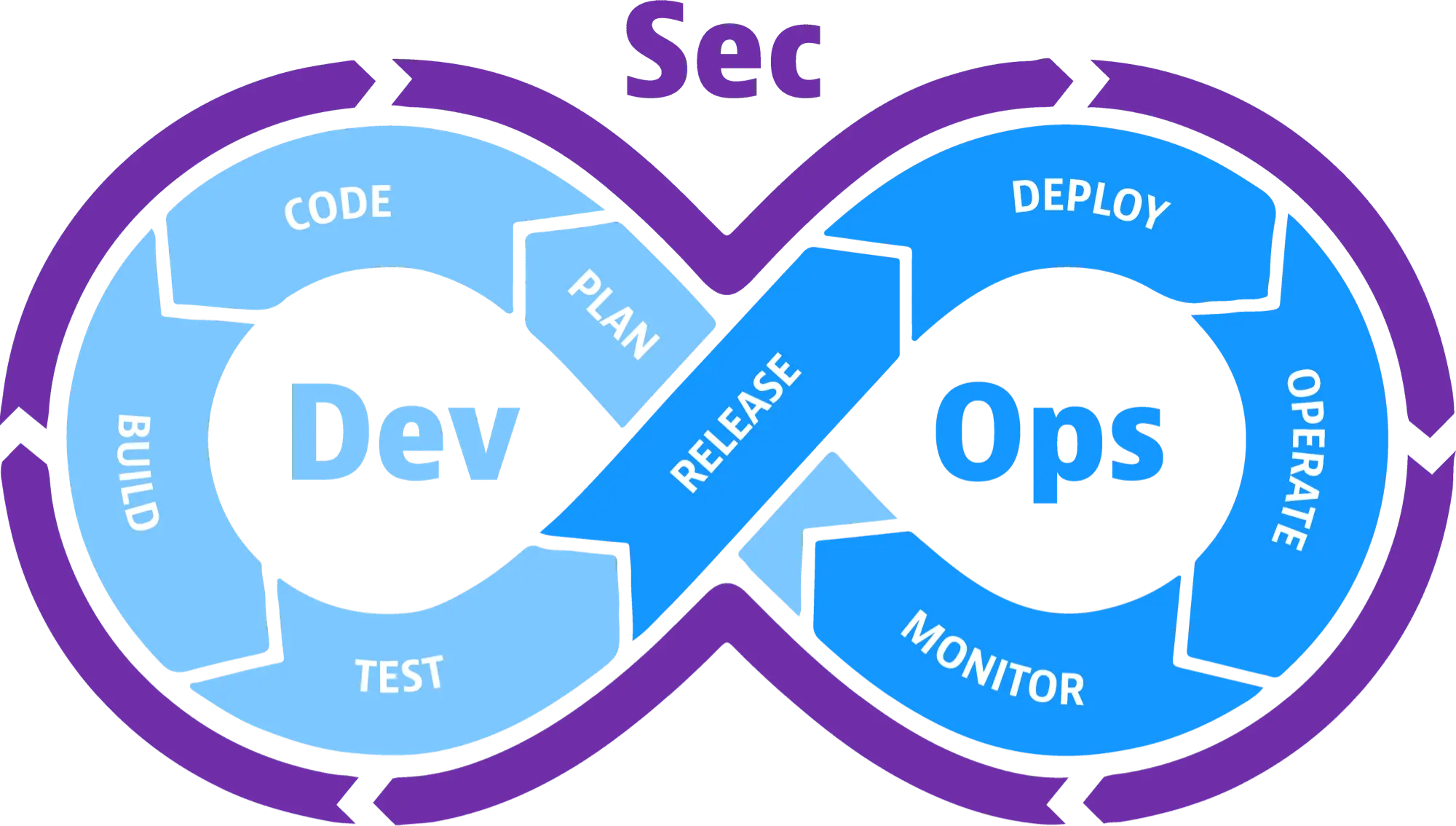
In this guide, we’ll explore the fundamental concepts of DevSecOps, understanding how it blends development, security, and operations to create a robust, secure, and efficient software development process. The diagram below outlines the key components that form the backbone of DevSecOps, each playing a vital role in ensuring the security of software from inception to deployment.
1. What is DevSecOps?
DevSecOps represents the convergence of Development (Dev), Security (Sec), and Operations (Ops) practices, emphasizing the importance of integrating security throughout the software development lifecycle. Unlike traditional approaches where security was often an afterthought, DevSecOps embeds security practices directly into the development and operations processes, ensuring that security is not just a final checkpoint but a continuous, integrated part of the entire workflow.
2. The Core Components of DevSecOps
The diagram above highlights the essential elements of DevSecOps, each of which contributes to a secure, efficient, and collaborative development environment. Let’s break down each of these components:
1. Automated Security Checks
Automated security checks are a cornerstone of DevSecOps, ensuring that security measures are applied consistently and efficiently throughout the development process. This includes:
SAST (Static Application Security Testing): Automatically scans the source code for vulnerabilities without executing the application. It helps identify potential security issues early in the development cycle.
DAST (Dynamic Application Security Testing): Tests the running application to find vulnerabilities that could be exploited in a live environment. It focuses on detecting issues like SQL injection, cross-site scripting, and other runtime vulnerabilities.
Why It Matters: By automating these checks, organizations can catch security flaws early, reduce the risk of security breaches, and maintain a higher standard of code security without slowing down the development process.
2. Continuous Monitoring
Continuous monitoring involves keeping a close eye on systems, networks, and applications in real-time to detect and respond to security threats promptly. Key aspects include:
User Activity Monitoring: Tracks user actions to detect suspicious behavior that could indicate a security threat.
System Logs: Continuously reviews logs to identify patterns or anomalies that could suggest a security breach.
Network Traffic Monitoring: Analyzes network traffic to detect and prevent unauthorized access or data exfiltration.
Why It Matters: Continuous monitoring ensures that any potential security issues are identified and addressed quickly, reducing the window of opportunity for attackers.
3. CI/CD Automation
Continuous Integration and Continuous Deployment (CI/CD) are fundamental practices in DevOps, and when integrated with security (DevSecOps), they ensure that security is embedded into every build, test, and deployment process:
Automated Builds and Tests: CI/CD pipelines automatically build the software and run tests, including security tests, ensuring that vulnerabilities are detected and addressed early.
Security Check Integration: Security checks are embedded into the CI/CD pipeline, ensuring that every update or deployment is secure before it reaches production.
Why It Matters: By automating the CI/CD process with integrated security checks, DevSecOps enables faster and more secure software releases, minimizing the risk of deploying vulnerable code.
4. Infrastructure as Code (IaC)
Infrastructure as Code (IaC) is a practice where infrastructure (networks, servers, databases) is managed and provisioned through code, allowing for automation and consistency:
Automated Provisioning: Automates the setup of infrastructure, ensuring that it’s secure and consistent across environments.
Configuration Management: Manages configurations through code, making it easier to enforce security policies and monitor changes.
Why It Matters: IaC reduces the risk of human error, ensures consistency, and allows for more robust security practices by treating infrastructure configurations as part of the software development lifecycle.
5. Container Security
Containers have become a popular way to deploy applications, but they also introduce new security challenges. DevSecOps addresses these challenges through:
Image Scanning: Scans container images for vulnerabilities before they are deployed.
Runtime Security: Monitors containers in real-time to detect and prevent security issues.
Why It Matters: Ensuring the security of containers is crucial as they are often used in production environments. By integrating container security into the DevSecOps workflow, organizations can deploy containers confidently, knowing they are secure.
6. Key Management
Managing secrets and keys securely is a critical aspect of DevSecOps, ensuring that sensitive information is protected:
API Key Management: Manages and rotates API keys securely to prevent unauthorized access.
Password Management: Ensures that passwords are stored securely and managed according to best practices.
Certificate Management: Manages SSL/TLS certificates, ensuring they are up-to-date and secure.
Why It Matters: Proper key management is essential for protecting sensitive data and ensuring that only authorized users and systems have access to critical resources.
7. Threat Modeling
Threat modeling is a proactive approach to identifying potential threats and vulnerabilities in the system:
Identifying Threats: Analyzes the system to identify potential threats that could exploit vulnerabilities.
Risk Assessment: Evaluates the likelihood and impact of each threat, prioritizing them based on risk.
Why It Matters: By identifying and addressing potential threats early, organizations can significantly reduce the risk of security breaches.
8. Quality Assurance (QA) Integration
Integrating QA into the DevSecOps process ensures that security is considered during testing, not just after development:
Embed QA in DevSecOps: QA teams work closely with development and security teams to identify and address security issues during testing.
Continuous Testing: Security tests are continuously run throughout the development process, ensuring that vulnerabilities are caught early.
Why It Matters: By embedding QA into the DevSecOps process, organizations can ensure that security is a continuous concern, not just a final check.
9. Collaboration and Communication
DevSecOps requires strong collaboration and communication between development, security, and operations teams:
Knowledge-Sharing Culture: Encourages teams to share knowledge and collaborate on security issues.
Integrated Tools: Uses tools that facilitate communication and collaboration across teams.
Why It Matters: Effective collaboration ensures that security concerns are addressed promptly and that everyone in the organization is aligned on security goals.
10. Vulnerability Management
Vulnerability management involves continuously scanning for and addressing vulnerabilities in the system:
Vulnerability Scanning: Regularly scans the system for known vulnerabilities.
Prioritize and Fix Vulnerabilities: Prioritizes vulnerabilities based on risk and implements fixes promptly.
Why It Matters: Regular vulnerability management helps ensure that security issues are identified and addressed quickly, reducing the risk of exploitation.
Conclusion:What is DevSecOps
DevSecOps is more than just a buzzword—it’s a fundamental shift in how security is integrated into the software development lifecycle. By embedding security practices into every stage of development and operations, DevSecOps helps organizations deliver secure software faster and more efficiently.
Whether it’s through Automated Security Checks, Continuous Monitoring, CI/CD Automation, or Infrastructure as Code (IaC), each component of DevSecOps plays a crucial role in ensuring that security is never an afterthought but a continuous and integral part of the process.
As cybersecurity threats continue to evolve, adopting DevSecOps practices is essential for any organization looking to stay ahead of the curve and protect its software and data. Start integrating DevSecOps practices today and ensure that your software development process is as secure as it is efficient.